Technology
Unlocking the Enterprise Buyer


As digital transformation accelerates, enterprises are rapidly shifting toward multicloud architectures to maximize scalability, cost-efficiency, and resilience. But this shift also presents unprecedented cloud security challenges-especially when it comes to IaaS security solutions.
To address these rising complexities, a global enterprise cloud security provider partnered with Jasper Colin to dive deep into the realities of securing multicloud environments. Their goal? To understand enterprise readiness, assess cloud security priorities, and unlock product-market fit (PMF) signals for a new generation of IaaS cloud security tools.
The study set out to answer four central research objectives:
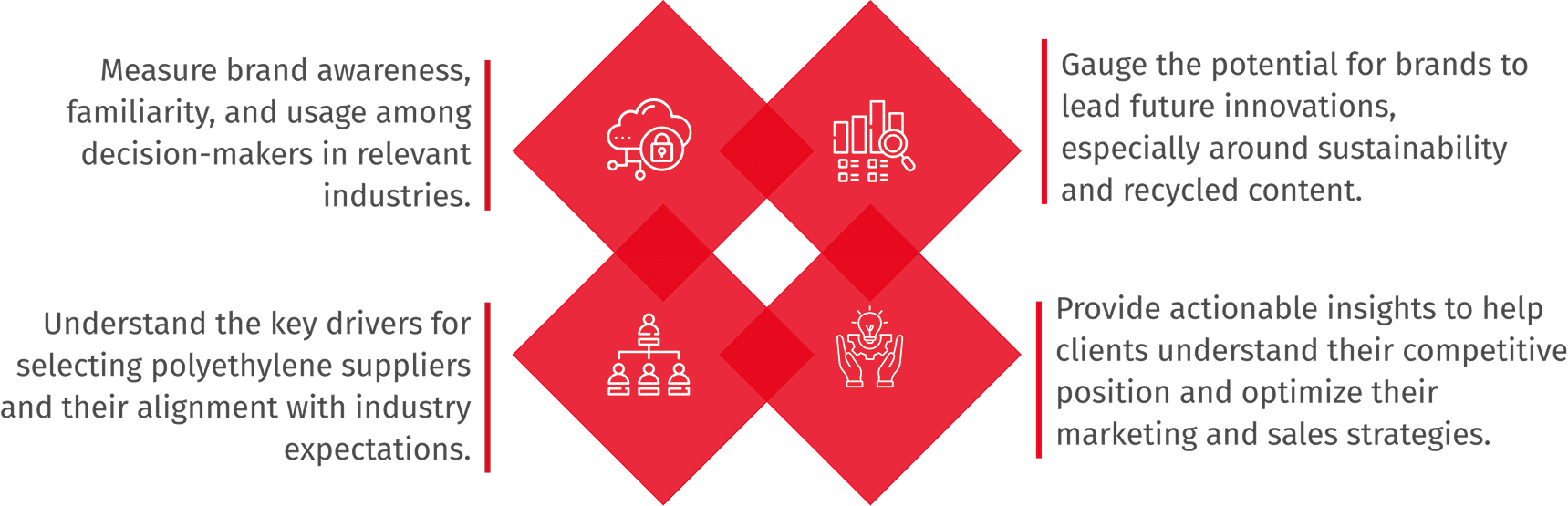
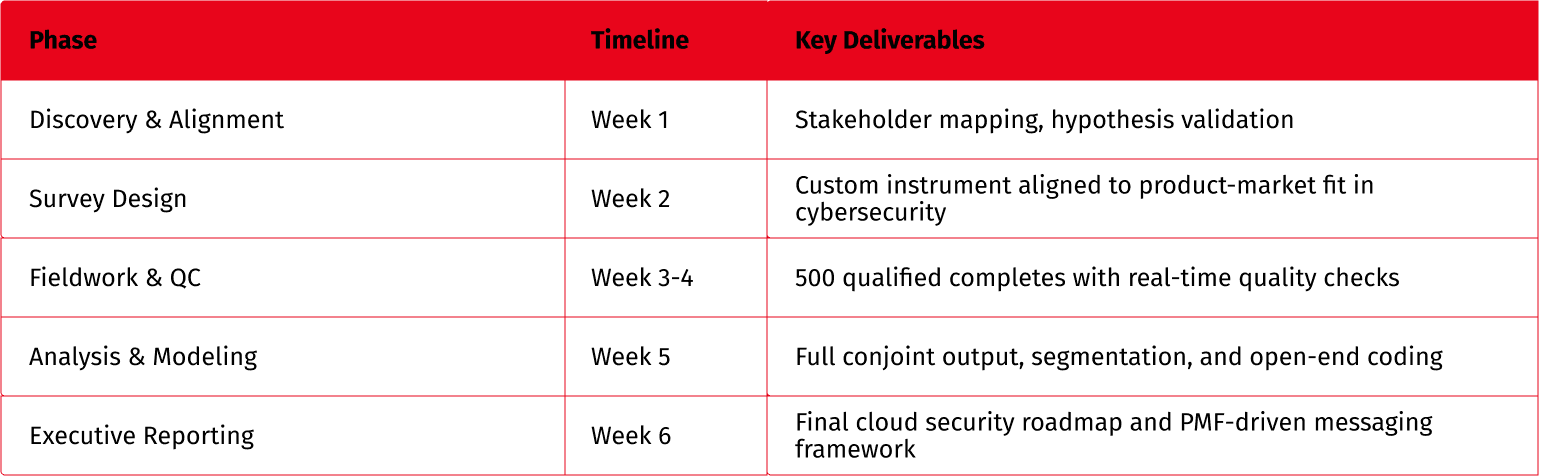
1. Immersion & Hypothesis Mapping
We began by aligning with client teams to refine the core hypothesis, focusing on:
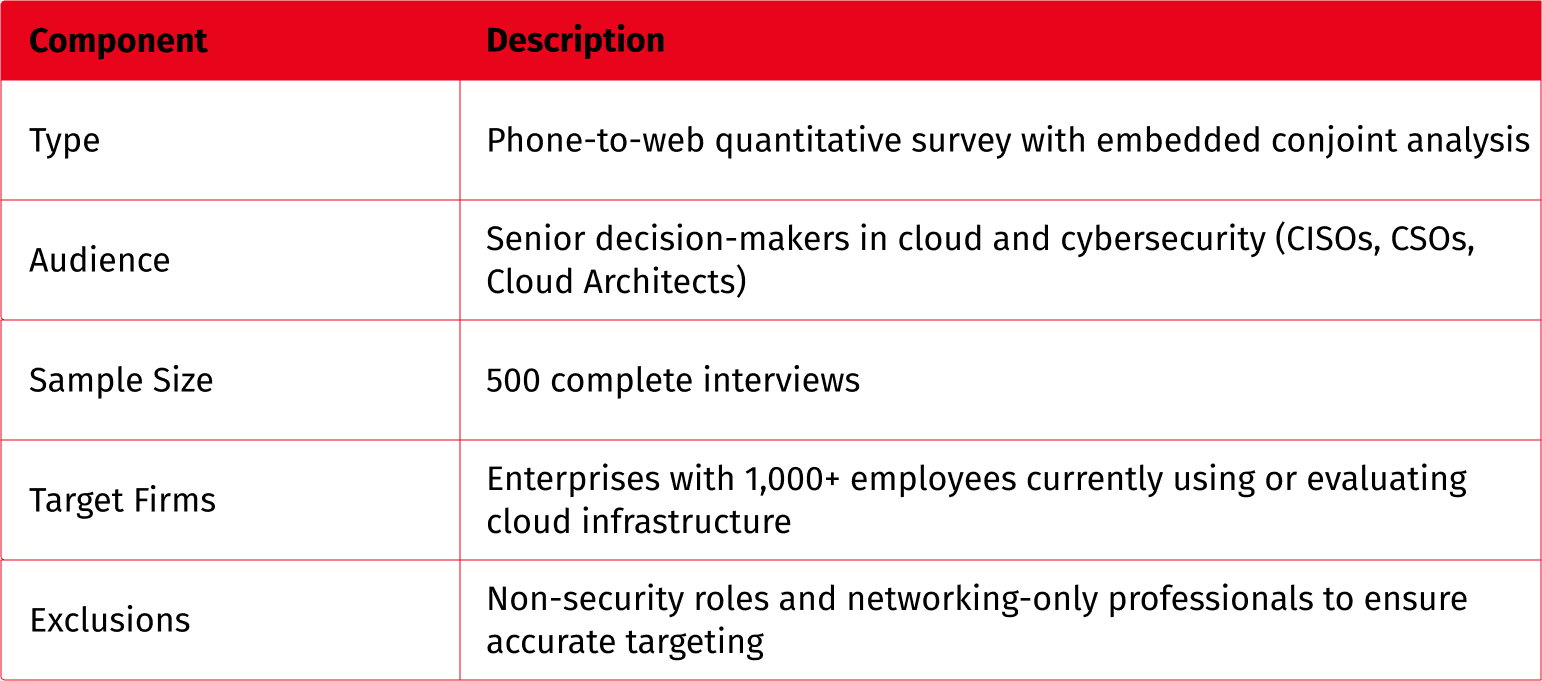
2. Screening & Profiling
Participants were carefully selected for their involvement in:
3. PMF Core Survey
The survey instrument captured:
4. Advanced Analytics
To extract deeper insights:
This strategic engagement enabled our client to:
In a cloud-native world, understanding the difference between SaaS, PaaS, and IaaS in the security context is no longer a luxury-it's a necessity. This study not only highlighted multicloud infrastructure security challenges but also delivered clear guidance on how enterprises secure multicloud environments today and what they'll need tomorrow.
By combining behavioral data, strategic segmentation, and PMF research for cybersecurity, the client is now better equipped to lead in a market where hybrid cloud migration security is at the heart of every digital transformation.